
Silicon-verified, production-proven eFPGA for MCU/SoC/custom ASIC applications - optimized for edge and endpoint AI processing, military and automotive.
QuickLogic has been supplying eFPGA-based products for consumer, industrial and mission-critical applications for nearly three decades. Our eFPGA IP enables SoC designers the flexibility to easily program custom functions, hardware accelerators and security capability after an SoC has been manufactured.
Benefits
- Expand addressable market of your SoC through on-chip reprogrammability
- Market test new features and functions before committing to hard gates or custom silicon
- Protect your ASIC by using the eFPGA as a reprogrammable isolation area for security or authentication IP
- Extends product longevity and hardware-based Continuous Integration (CI)
Features
- High-performance architecture for low power applications
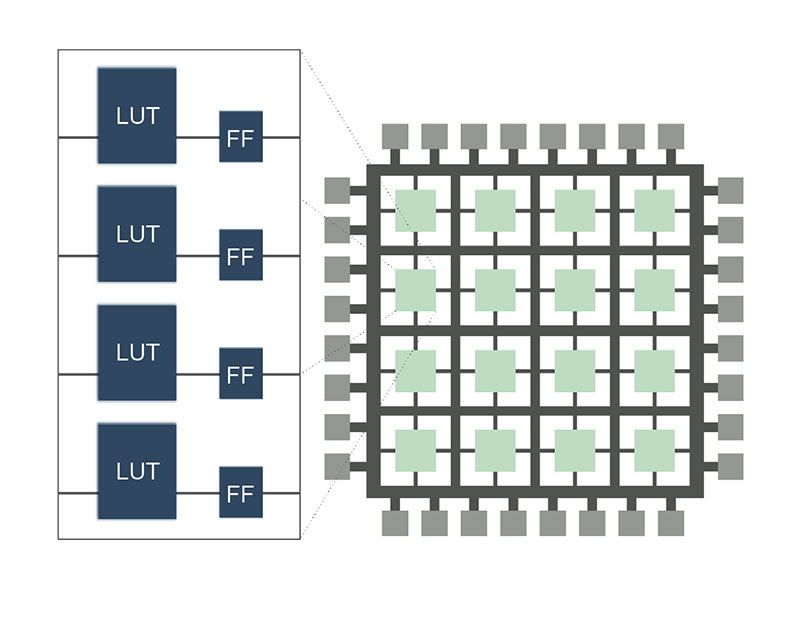
- Super Logic Cell (SLC) clusters 4 logic cells together with hierarchical routing networks for optimum performance and power consumption
- Each logic cell can be used as two separate 4-input LUTs or one 5-input LUT.
- Direct input selection to the register allows combinatorial and sequential logic to be used separately.
- Multiple outputs per logic cell are strategically selected to either feedback within the same SLC or to travel out to another SLC. A shared register clock, set, and reset signals for all four logic cells helps reduce routing congestion.
- Array sizes ranging from 8×8 SLC up to 64×64 SLCs
Resources
QuickLogic ArcticPro 2 eFPGA IP and FPGA Software for GLOBALFOUNDRIES 22FDX
Applications
Defense
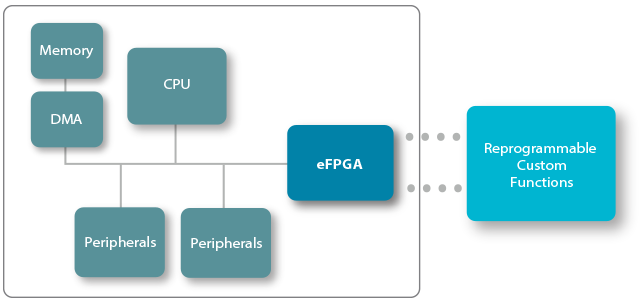
eFPGA is an ideal platform for updating and changing functions / algorithms, especially for systems that are deployed in the field where access is difficult
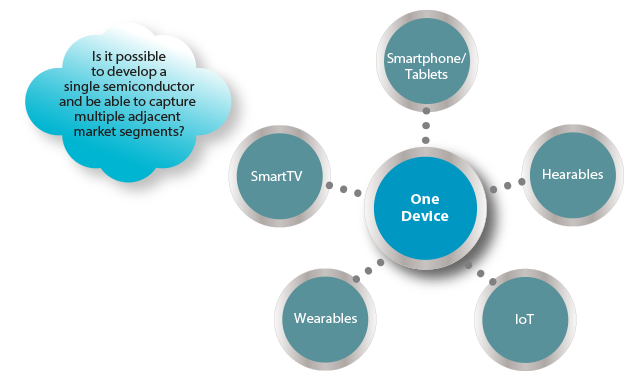
IoT - Addressing Multiple Markets with One Device
Security
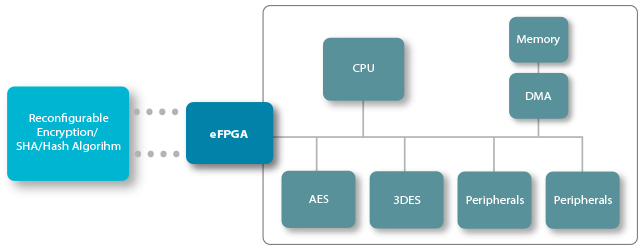
Common security algorithms can be implemented as hardened functions, but customers often prefer to have their own security algorithm on top of common security algorithms in order to make their application more secure.
“With the growth of the IoT market, a new set of applications and devices are driving the need for differentiated silicon solutions. We are pleased to work with QuickLogic as their years of experience with FPGAs will help FDX-based SoC designers to gain a critical time-to-market advantage for IoT applications.”
Mark IrelandVice president of ecosystem partnerships at GlobalFoundries

Ecosystem Partners



